
In the era of cloud computing, data security is a top priority. While AWS expertly manages the storage of data within its data centers, the responsibility for configuring data accessibility falls upon us.
Amazon S3 buckets are widely used by organizations, offering a highly scalable and durable object storage service through Amazon Web Services (AWS). However, the importance of securing your S3 buckets cannot be overstated, as even a minor oversight can result in unauthorized access to sensitive information.
This blog post explores how to prevent unauthorized access to your S3 buckets using CloudFront Origin Access Identity (OAI).

Understanding the Issue
By default, S3 buckets are private. However, when hosting a static frontend website, it’s common to grant public access to your bucket and enable the static web hosting property. Even with security policies applied to your bucket objects, a small mistake or incorrect configuration can lead to unauthorized access to sensitive data.
This is where CloudFront Origin Access Identity (OAI) comes to the rescue!
CloudFront Origin Access Identity
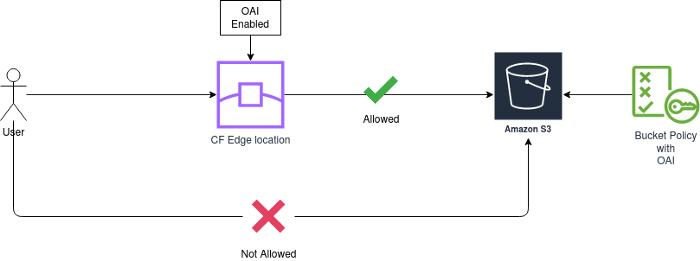
AWS CloudFront is a content delivery network (CDN) service that can be used to distribute content globally while providing a security layer. CloudFront OAI is a feature that helps secure your S3 buckets by allowing you to restrict access to your data to only what CloudFront distributes.
Let’s look into how we can configure Cloudfront on top of our S3 bucket.

Step 1: Setup S3 bucket
- Create an S3 bucket with “ACLs Disabled” and the “block all public access” setting.
- Upload all your frontend static content into this bucket.
Note: If you already have a static frontend hosted on S3, make sure to disable the static website hosting property, remove any existing bucket policies, and disable public access to your bucket.
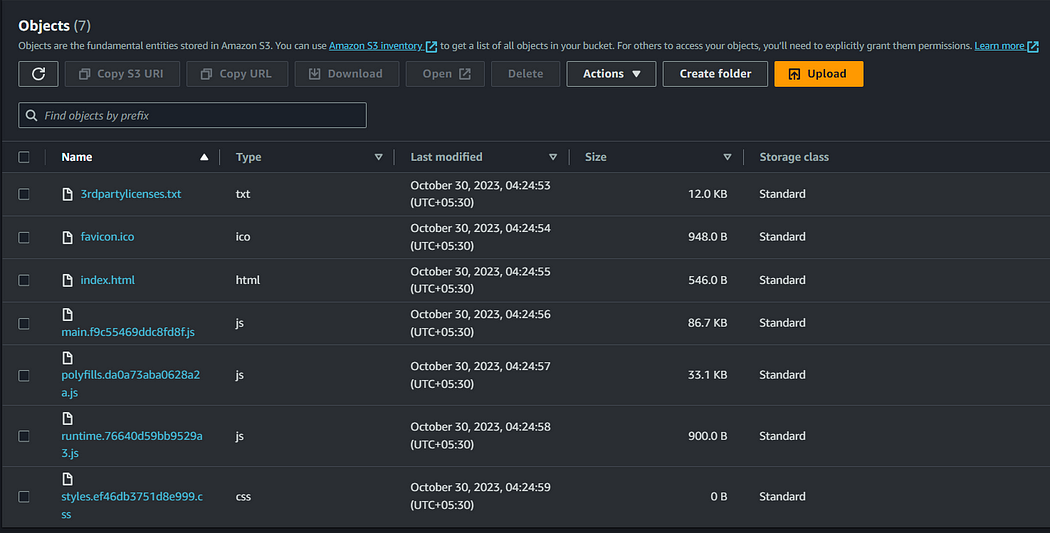
Step 2: Create a cloudFront distribution
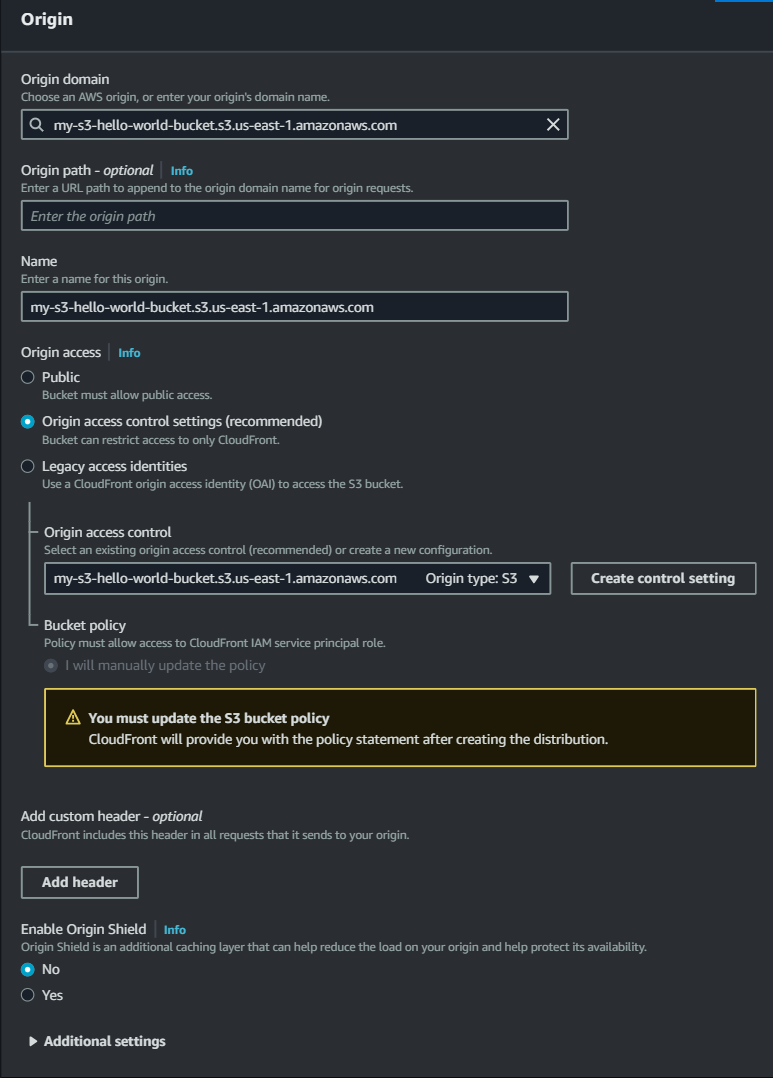
- Access the AWS Management Console and search for CloudFront, then create a new distribution.
- Choose your S3 bucket as the origin domain.
- Configure the origin access control settings.
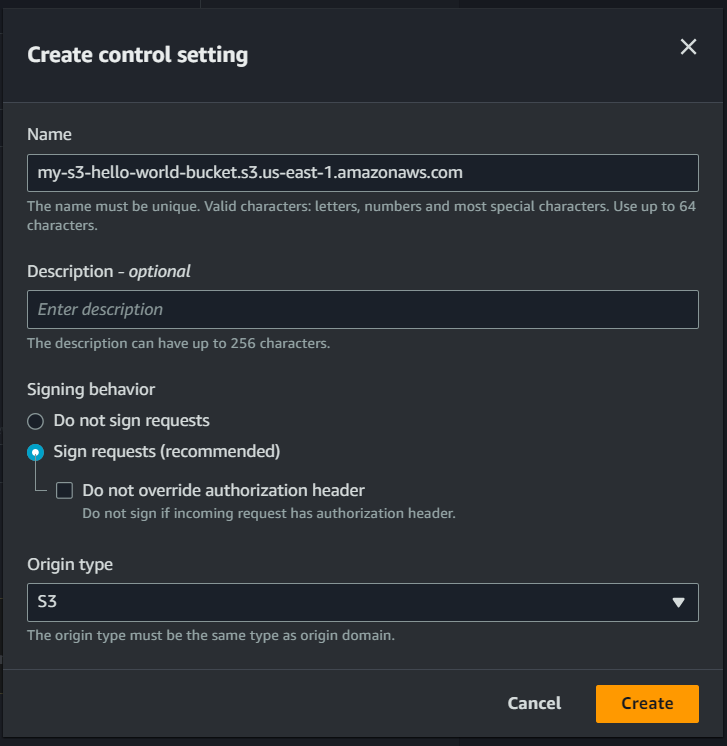
- Create control setting for origin access control.
- Keep the default cache behavior settings.
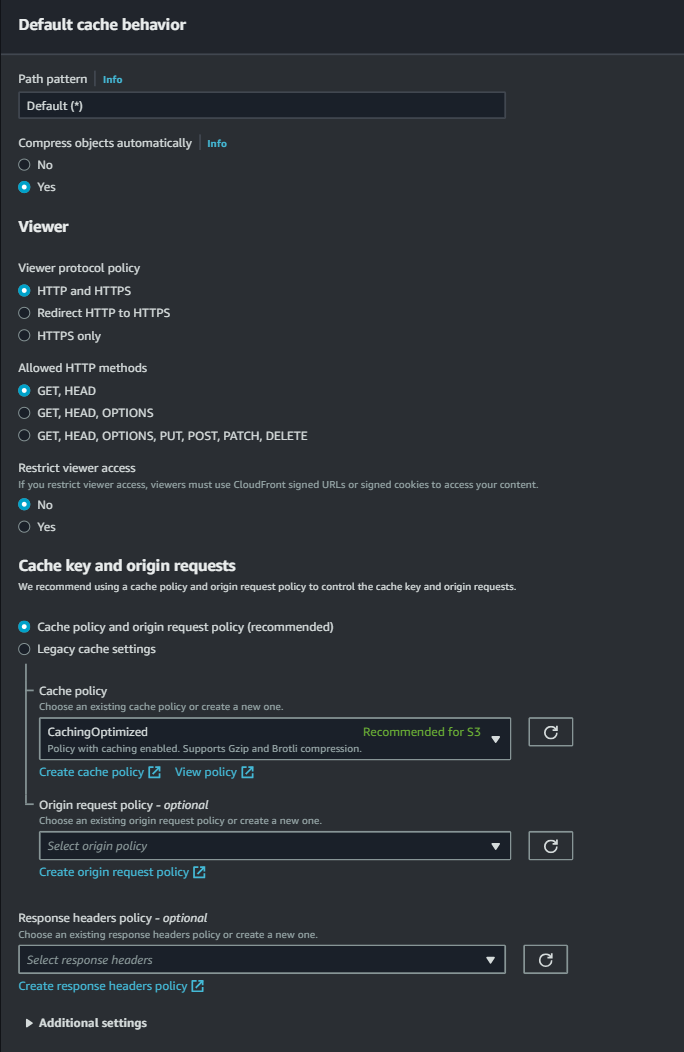
- Functional associations will be kept as default.
- Under Web Application Firewall (WAF), enable WAF for additional security if needed; otherwise, select “do not enable security protections”.
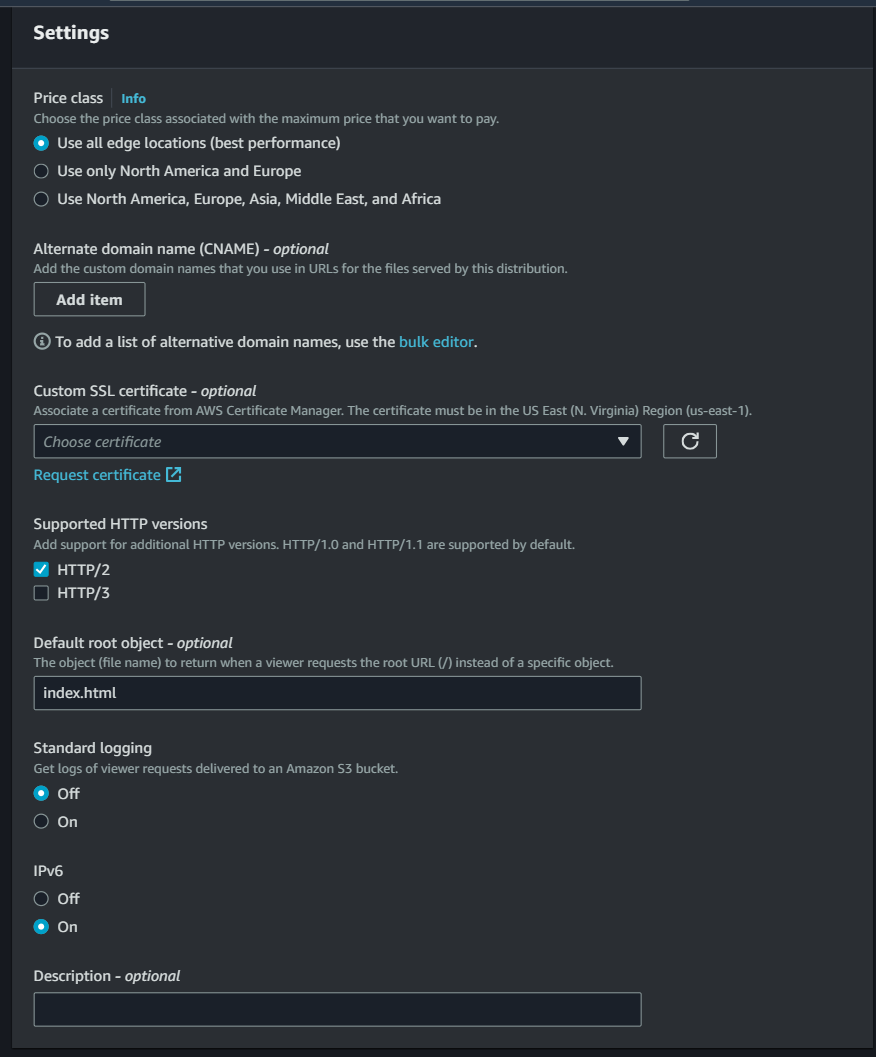
- Under settings, add “index.html” for default root object and create distribution.
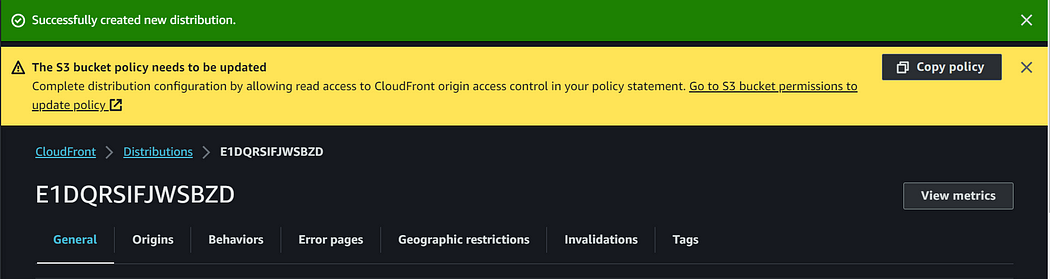
Step 3: Restrict bucket access
Once you’ve created a CloudFront distribution, you’ll find an option at the top of your AWS Management Console. Click “copy policy” and paste the policy into your configured S3 bucket policy.
Your bucket policy will look like the following 👇{
{
"Version": "2008-10-17",
"Id": "PolicyForCloudFrontPrivateContent",
"Statement": [
{
"Sid": "AllowCloudFrontServicePrincipal",
"Effect": "Allow",
"Principal": {
"Service": "cloudfront.amazonaws.com"
},
"Action": "s3:GetObject",
"Resource": "S3_BUCKET_ARN/*",
"Condition": {
"StringEquals": {
"AWS:SourceArn": "CLOUDFRONT_DISTRIBUTION_ARN"
}
}
}
]
}
Step 4: Test your Website
Retrieve your CloudFront distribution domain name and verify your website’s availability.
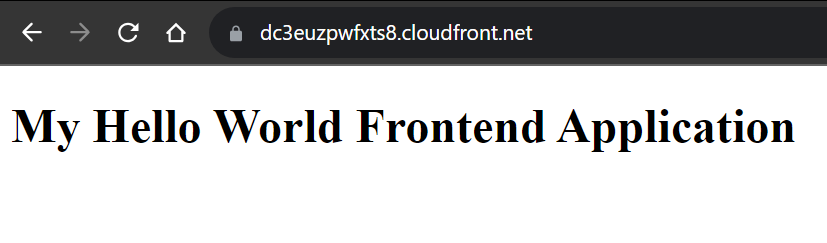
You can also assess the security of your “index.html” object by accessing its object URL.
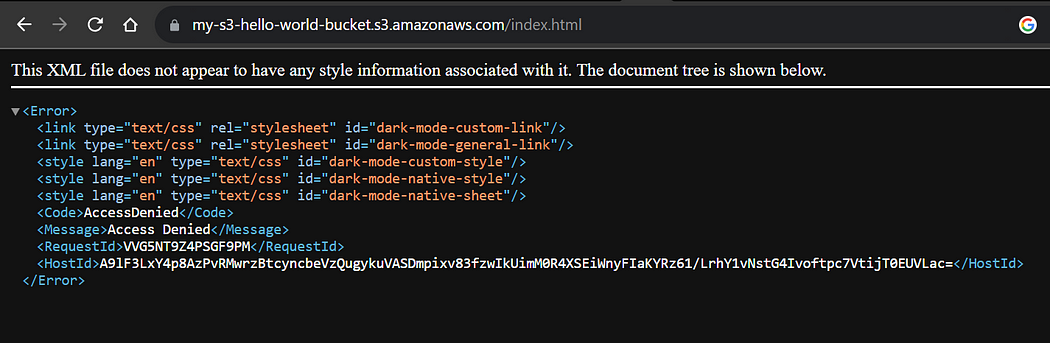
This indicates that your bucket is exposed only to your created cloudfront distribution and cannot be accessed directly, which ensures any unauthorized or direct access to your S3 bucket.
Conclusion
I hope you are now clear with how to use S3 for static hosting, cloudFront configuration and securing sensitive data in your S3 bucket using CloudFront OAI. This practice effectively restricts direct access to your content and improves content delivery performance.
If you found this post helpful, give it a 👏 and follow for more useful blogs. Thanks, and have a great day!

