In the ever-evolving world of Information Technology, the shift from traditional data centers to cloud computing has become a defining trend. Cloud computing offers unparalleled flexibility, scalability, and accessibility, prompting companies worldwide to migrate their operations to the cloud. However, this transition brings forth a new set of challenges, particularly concerning security.
Cloud service providers operate under a shared responsibility model, where they assure the security of the cloud infrastructure itself, but the responsibility for securing the workloads and data within the cloud falls squarely on the customer’s shoulders. This distinction underscores the importance of implementing robust security measures and adhering to best practices to safeguard against potential threats, data leaks, and hacking incidents.
In this blog post, we’ll delve into securing one of the most critical components of cloud applications: the database. We’ll explore essential best practices for protecting your database workloads in the cloud, including managing the database privately to avoid any public connections, utilizing a proxy to enhance efficiency and manage the number of database connections, and implementing an SSH tunnel for secure local database access.
Introduction
Before we delve into securing database access in the cloud, let’s understand some key concepts:
Amazon Relation Database Service (RDS)

Amazon RDS is a managed database management service offered by amazon. It simplifies the setup, operation, and scaling of relational databases, offering support for various database engines like MySQL, PostgreSQL, Oracle, SQL Server, and Amazon Aurora.
One key strategy for enhancing the security of RDS instances is to deploy them within a private subnet of your Virtual Private Cloud (VPC). This “private RDS” setup ensures network isolation, making the database inaccessible from the internet and reducing the attack surface.
By leveraging VPC security groups and network ACLs, you can control access to the database, meeting compliance requirements and enhancing overall security.
Database Proxy: RDS Proxy
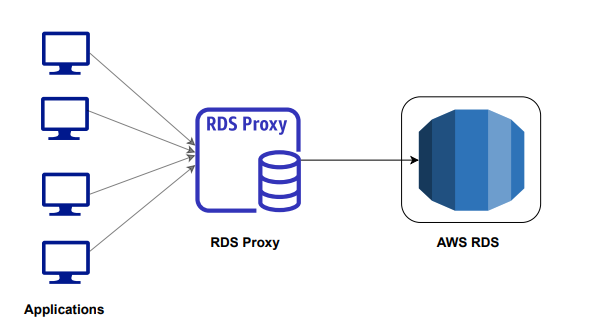
RDS Proxy serves as an intermediary between client applications and database servers, offering significant performance, scalability, and security benefits.
With RDS Proxy, you can efficiently manage database connections through features like connection pooling, load balancing, and query caching which reduces the overhead of establishing new connections, while load balancing distributes incoming connections evenly across multiple database instances, enhancing scalability.
Additionally, query caching reduces database load and boosts performance by caching frequently executed queries.
Furthermore, RDS Proxy supports IAM authentication, minimizing the risk of unauthorized access and enhancing security.
SSH Tunneling for Secure Access
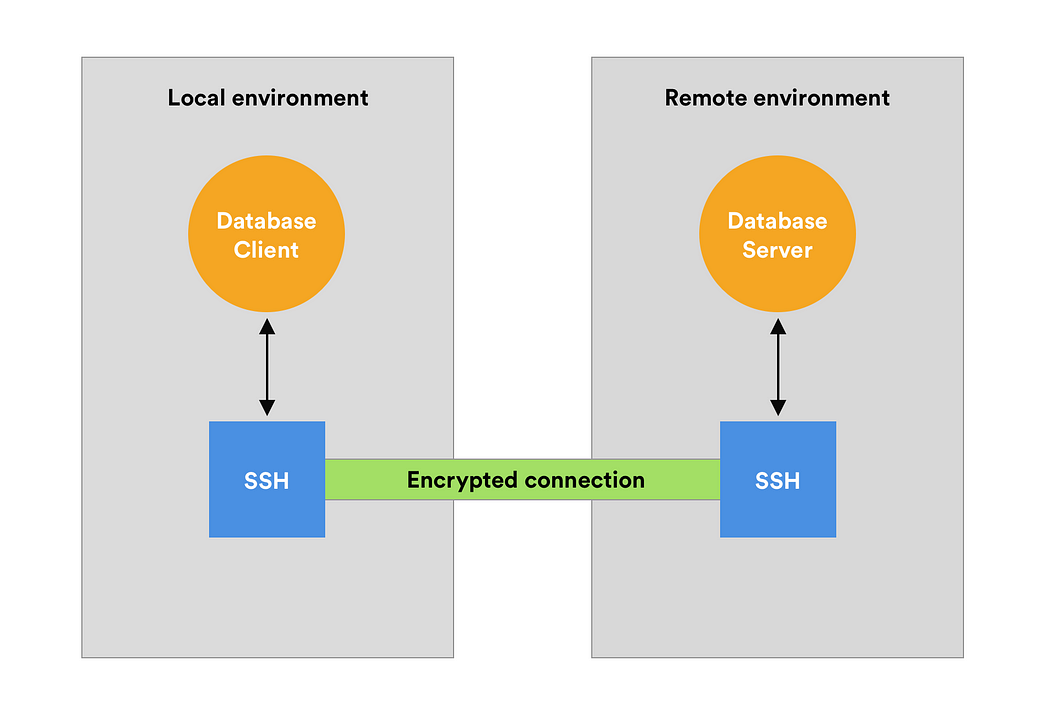
SSH tunneling provides a secure method for establishing communication between a local computer and a remote server, commonly used for accessing resources on private networks or behind firewalls. By creating an SSH tunnel, you can securely access your RDS instance from your local machine.
This setup encrypts network traffic, ensuring data privacy and integrity, and enables access to private resources securely. SSH tunnels also offer a simplified setup process, providing a straightforward method for establishing secure connections without exposing sensitive information.
Now that we’ve covered the key concepts, let’s dive into the practical implementation.

Before We Begin
Let’s take a moment to outline our goals and what we aim to achieve:
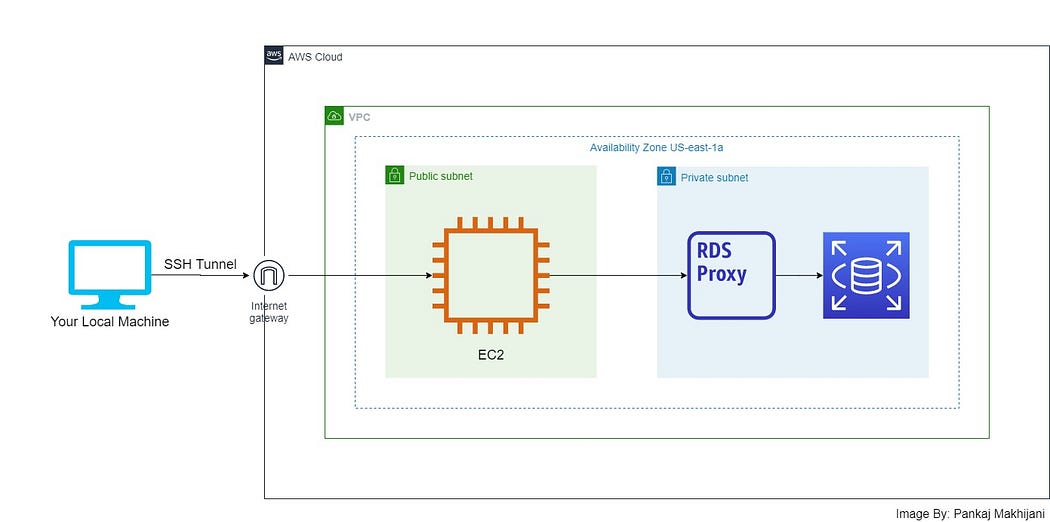
Above is the infrastructure diagram illustrating the implementation of secure access to RDS with a private subnet, RDS Proxy, and SSH tunnel. It highlights the various resources involved, such as EC2 instances, RDS instances, proxies, and networking components.
No need to be concerned; it’s not as complex as it appears. We’ll break down each step into manageable tasks and simplify the process.
Before we begin, ensure you have the following prerequisites:
Prerequisites
- An active AWS account
- Basic understanding of AWS cloud, network, and database
Now, let’s get started.
Step 1: Setting up the AWS network.
To start, log in to the AWS Management Console and navigate to the VPC dashboard. Create a new VPC with both public and private subnets, where our database will reside.
Select the VPC option and proceed to create it. Provide a name and CIDR range for the VPC. We’ll need one Availability Zone (AZ) with one public and one private subnet. Since we don’t require NAT gateways and VPC endpoints at the moment, simply review the settings and click on “Create”.
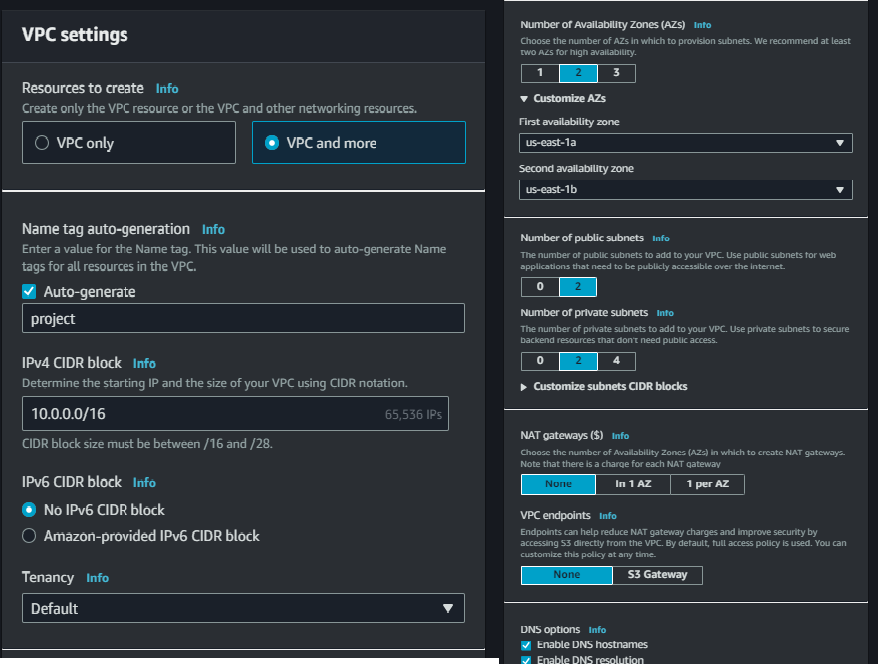
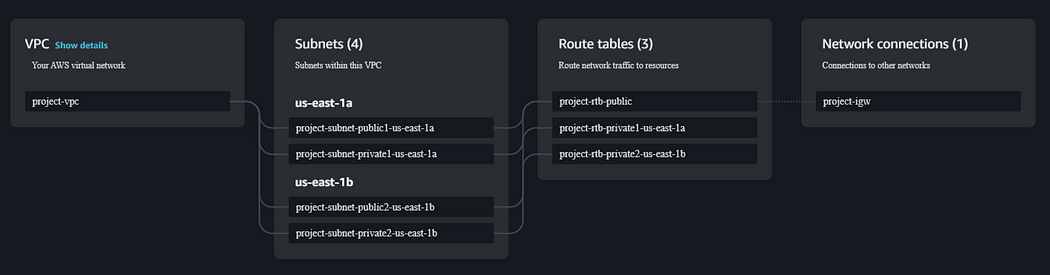
Step 2: Creating an RDS Instance in the Private Subnet
With the network infrastructure in place, it’s time to provision our RDS instance. Navigate to the RDS dashboard and proceed to launch a new RDS instance.
Please note that we will be creating the database with basic configurations and without additional monitoring and backup requirements. However, you have the option to enable these settings according to your needs.
Select the “Standard create” option and choose the PostgreSQL database with the free tier template. Keep the master username as “postgres” and provide a password of your choice. For the instance class, select “t3.micro” with 20 GB gp3 storage and disable autoscaling.
Under the connectivity settings, disable public access and select “Create new security group”. Do not select the checkbox for proxy integration at this stage, as we will set it up separately after creating the database.
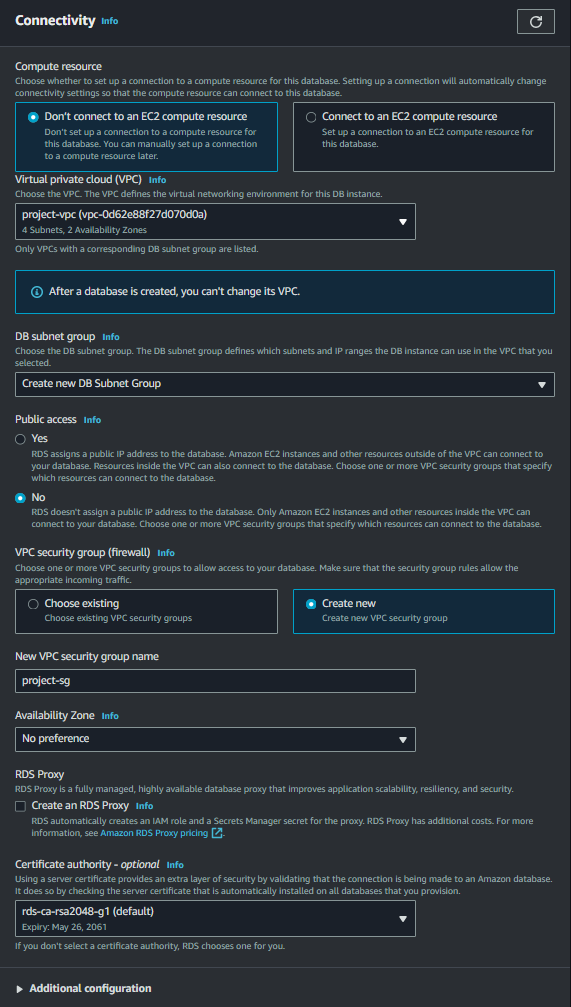
Here, we are not selecting the checkbox for the proxy integration, as we will set it up separately after creating the database.
Click “Create” and wait for a few minutes until it is created.
Step 3: Configuring RDS Proxy
Once the RDS instance is up and running, navigate to the RDS Proxy dashboard and create a new proxy for your RDS instance.
Select “PostgreSQL” as the engine family, provide an identifier name for your proxy, and select your database as the target group configuration.
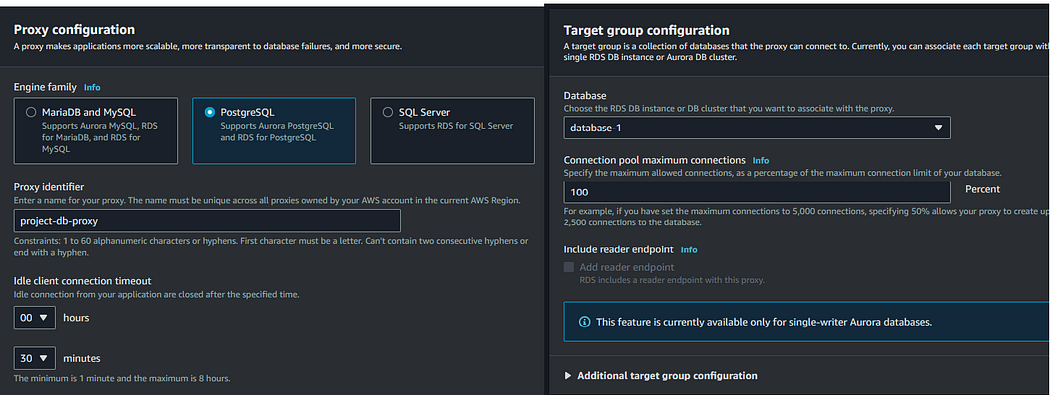
For authentication, the proxy checks the connection request with the database credentials stored in the secrets manager. Let’s create a secrets manager secret to store credentials for authenticating connections to the proxy.
Creating Secrets in Secrets Manager
Select the secret type as “Amazon RDS database” and enter your database credentials. The encryption key will be default, and select your RDS database.
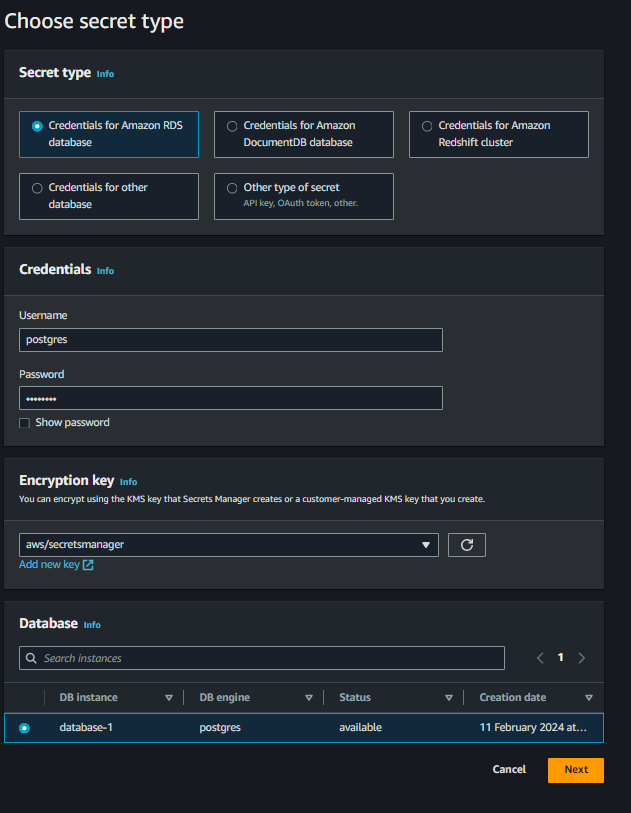
Provide a name and description for the secret in the “Configure secret” page, then click “Next”.
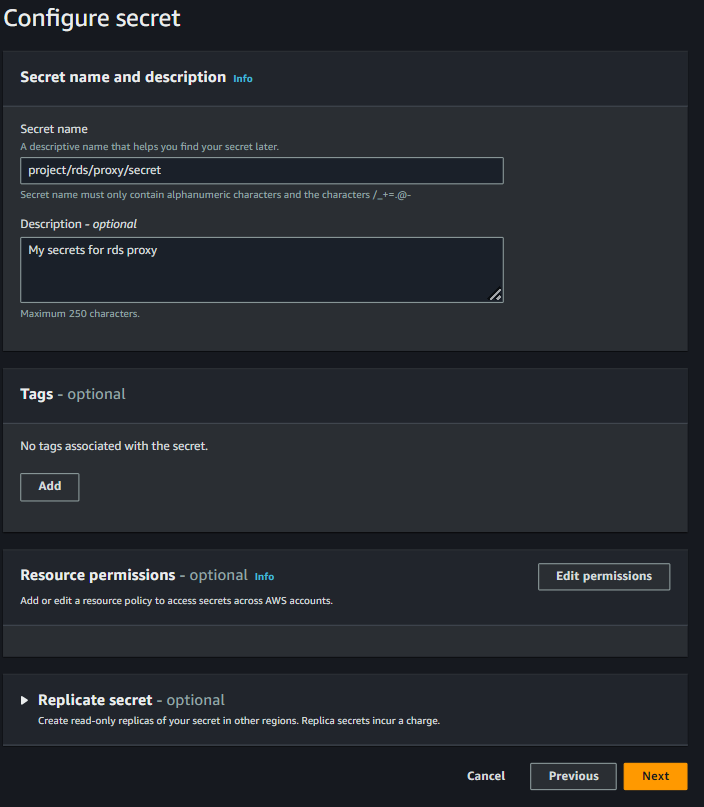
Automatic rotation of secrets is not required in our case, so turn it off. Review the settings and create your secret.
Once the secret is created, navigate back to the proxy creation page and select the created secret key for proxy authentication.
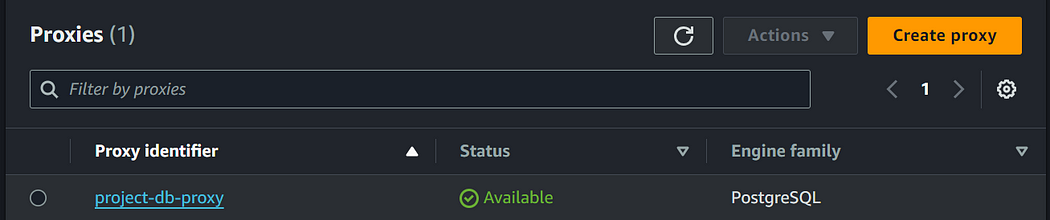
Under the proxy connectivity settings, select the subnets, create a new security group for the proxy, and then click “Create Proxy”.
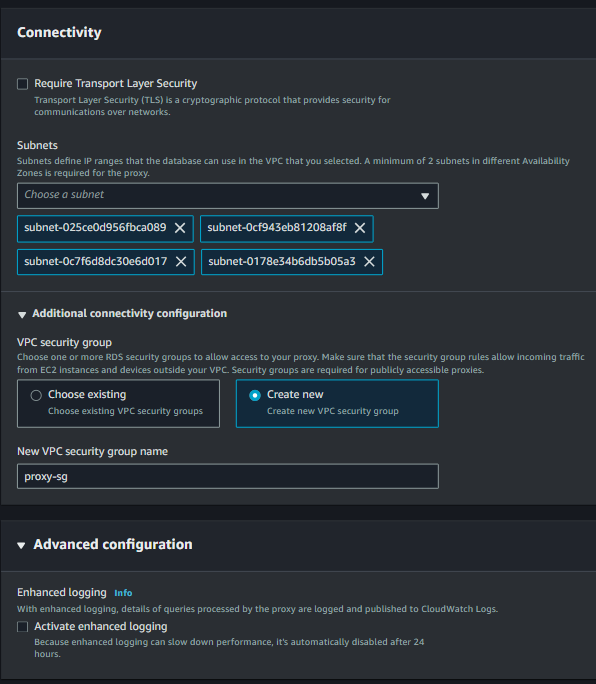
Wait till the time database proxy gets provisioned for you.

Once created, let’s navigate to the security group and grant the proxy security group access to the PostgreSQL port.
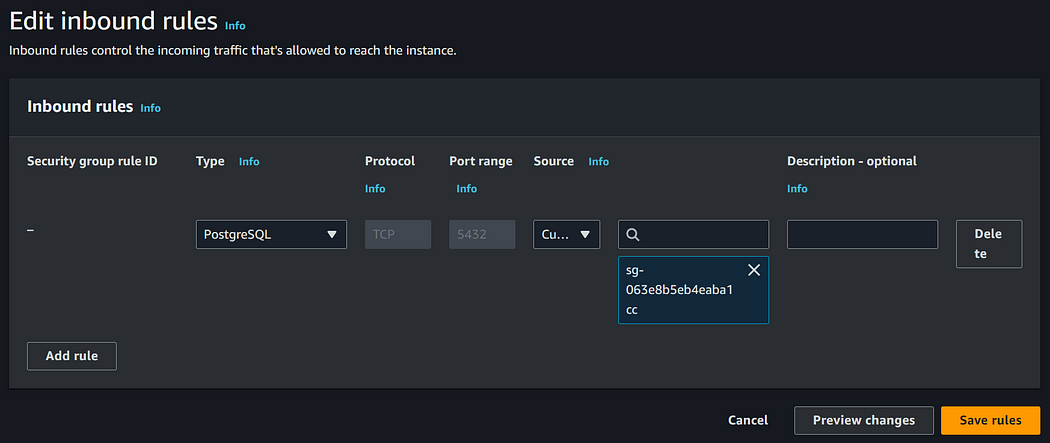
Additionally, navigate to the proxy security group and allow access from the VPC.
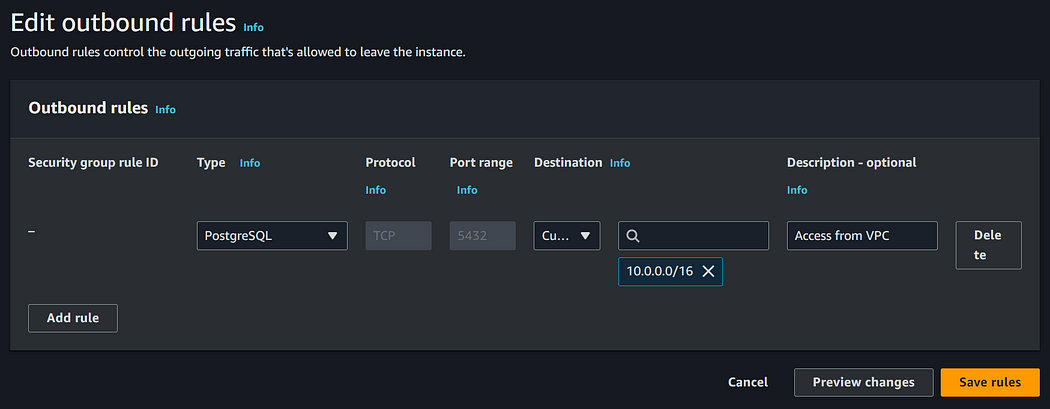
Now, you are ready to connect the compute resources or run applications from the VPC to connect to your database via the proxy. Additionally, you can also allow access from specific resource security groups for more granular access and additional security for your database.
With our application up and running after connecting to the database, let’s proceed to set up an SSH tunnel to access the database from our local machine and inspect its contents.
Step 4: Creating an EC2 Instance for SSH Tunnel
To establish a secure SSH tunnel to our RDS instance, we’ll create an EC2 instance in a public subnet. This EC2 instance will serve as our bastion host, allowing us to securely connect to our RDS instance located in the private subnet.
Navigate to the EC2 dashboard and proceed to launch a new EC2 instance. Choose an Amazon Linux Amazon Machine Image (AMI) and select an instance type that suits your needs.
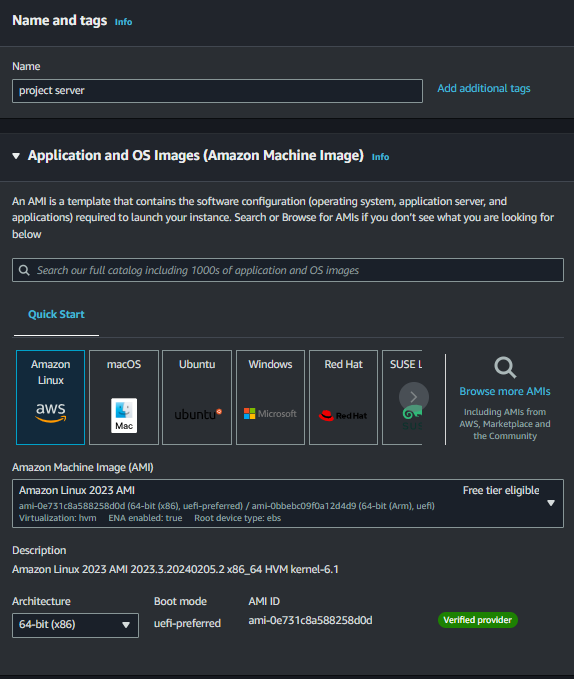
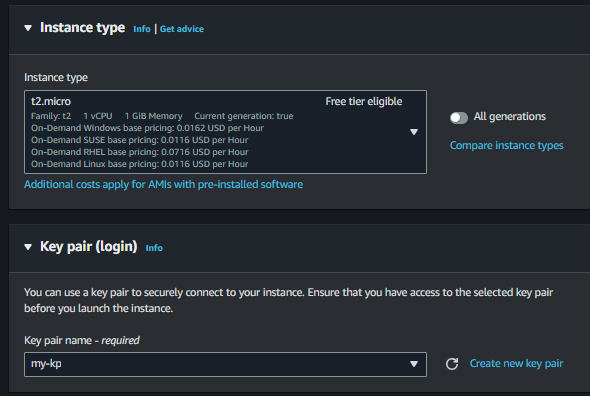
Ensure that you select a public subnet for the EC2 instance, as it will require internet connectivity to establish the SSH tunnel.
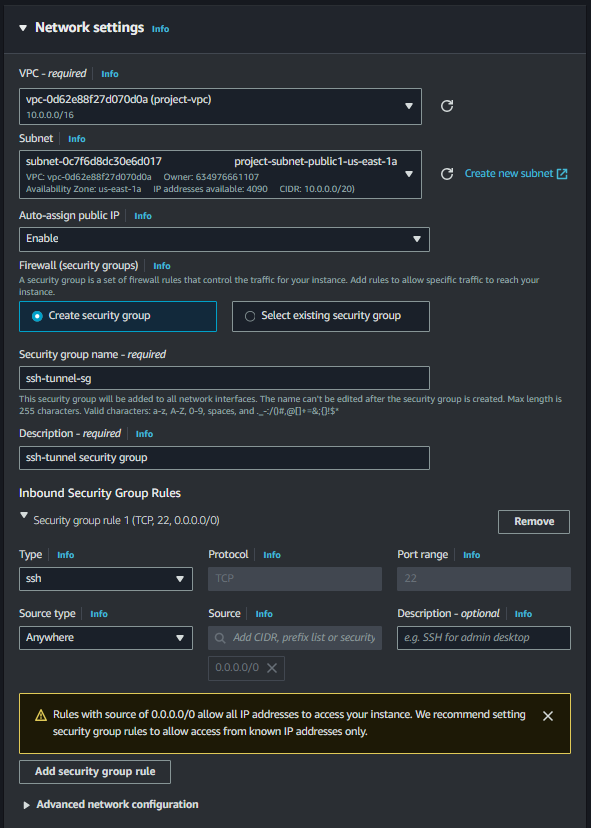
Keep the rest of the configurations unchanged and click “Create”. Then, wait for the EC2 instance to spin up.
While waiting, you can take a break and grab a cup of tea or coffee, as we are almost there.

Our instance is now in the running state. Let’s verify the security configuration to avoid any errors during testing the connection.

Step 5: Security Walkthrough
- Navigate to the RDS security group and verify that it only allows connections from the RDS proxy security group.
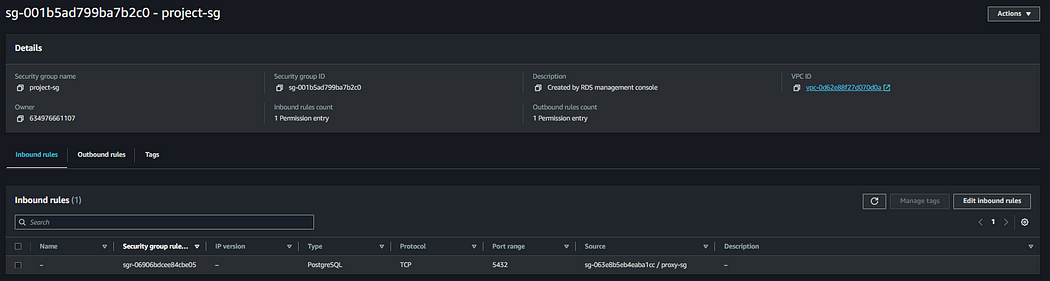
2. Check the Proxy Configurations
Navigate to the created proxy and verify that the proxy endpoint and target are in the “Available” state. Also, ensure that the secret specified for authentication contains the proper RDS credentials.
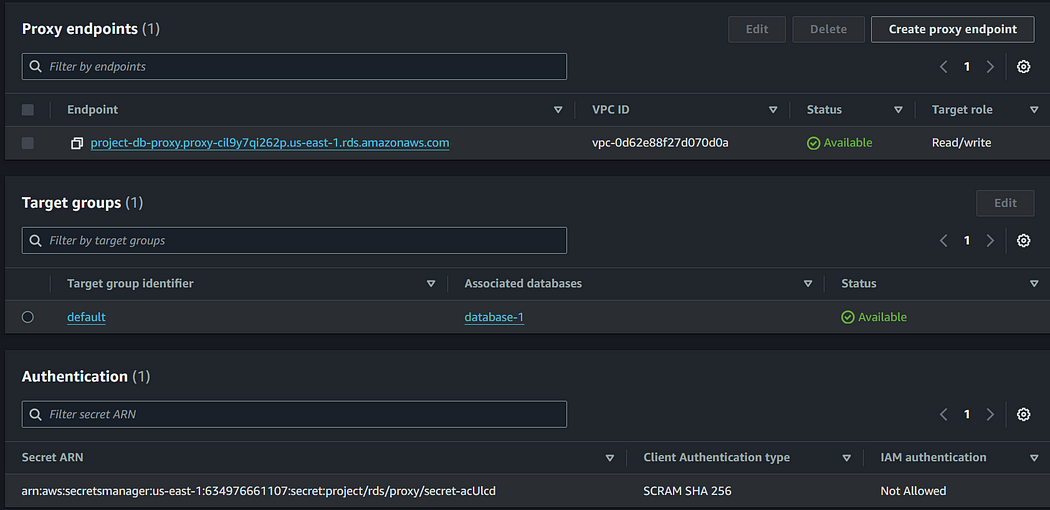
Next, navigate to the RDS proxy security group and allow access from the EC2 instance security group. This action will permit connections from the SSH tunnel to the proxy endpoint.
As a security best practice, going forward, when providing database access to resources or services, allow access only from specific service or resource security groups.
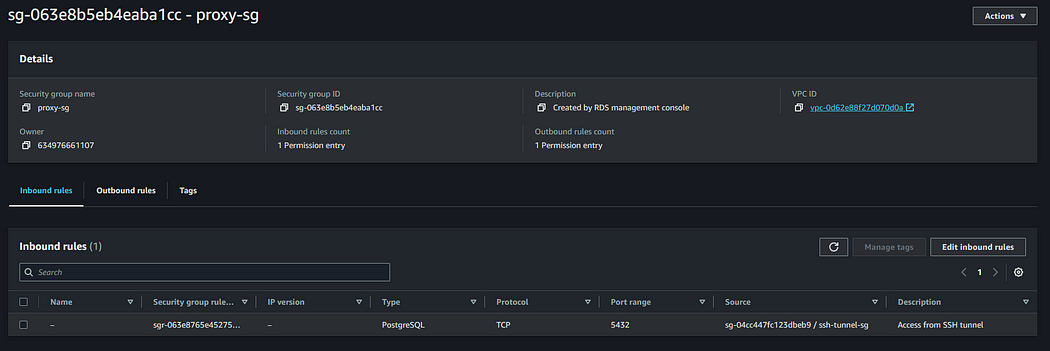
3. Check the SSH Tunnel Configurations
Verify that you have spun up your SSH tunnel EC2 instance in a public subnet and enabled a public IP for it. Additionally, check its security group settings and ensure that only your machine’s IPv4 address, from which the database needs to be connected, is allowed.
This ensures that only authorized connections are permitted to the SSH tunnel.
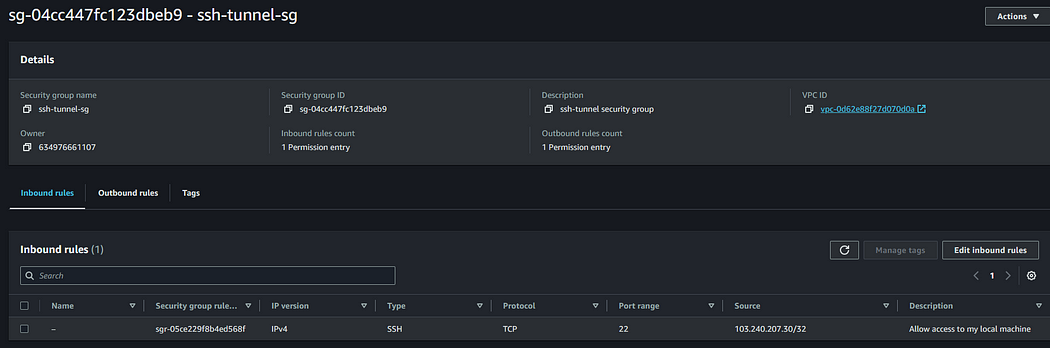
If you have successfully implemented the above steps, we are ready to proceed with testing our setup.

Step 6: Testing the Setup
Now that we’ve completed the setup of our secure access to RDS with a private subnet, RDS Proxy, and SSH tunnel, it’s time to test the configuration to ensure everything is working as expected.
For testing purposes, I will be using the DBeaver database tool.
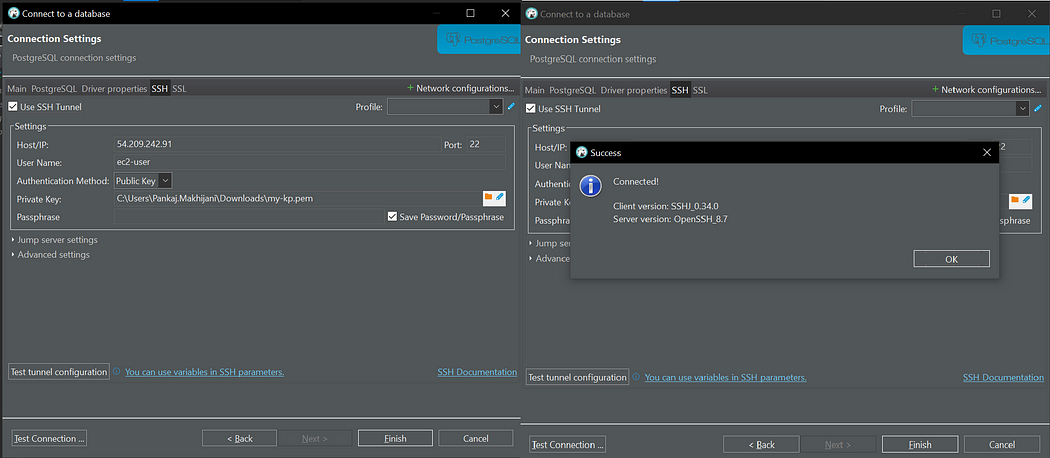
As you can see, we have successfully established the connection with our SSH tunnel. Now, let’s proceed to test the proxy endpoint connection.
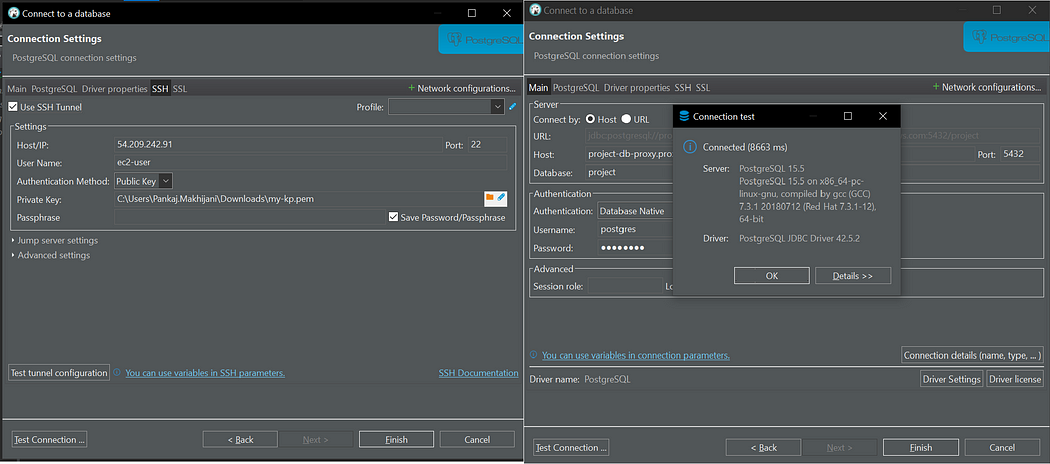
We can successfully connect to our database via our proxy endpoint. 🎉

I hope you are also able to securely connect to your RDS database using the proxy and SSH tunnel. If you encounter any issues, please feel free to leave a comment, and I’ll be happy to assist you.
Conclusion
In this blog, we’ve explored the steps to secure access to our RDS database using a private subnet, RDS Proxy, and SSH tunnel. By implementing these measures, we’ve significantly enhanced the security of our database infrastructure in the cloud.
I hope you found this content informative and enjoyable. For more blogs and updates, please consider following and clicking the 👏 button below to show your support. Happy coding! 🚀
Thank you for reading! 💚
