
In this era of cloud computing and container orchestration, security is a top most priority. Whether we’re running a small-scale web service or a complex, distributed application on Amazon Elastic Container Service (ECS), keeping sensitive information, such as API keys, database credentials, and other secrets, safe from getting compromised is essential.
But, how can we ensure that application secrets are stored and managed securely on ECS? This is when AWS parameter comes into picture.
In this blog post, we’ll explore what is AWS Parameter store and how we can use it effectively to store and manage our application secrets.
AWS Parameter Store
AWS Parameter Store is a service provided by Amazon Web Services that offers a centralized and secure way to store and manage configuration data, including application secrets. AWS Parameter store is a part of AWS Systems Manager, a suite of services designed to help you manage your AWS resources efficiently. Some of the key features of AWS includes Secure Storage, Hierarchical Structure and Versioning.
Implementing AWS Parameter Store with ECS
Here, I have used the demo node-js application that I will be using to demonstrate the use of AWS Parameter store. You can use it too to follow along with me. Containerize the application and push it onto ECR.
Here’s a step-by-step guide for using AWS Parameter Store to secure your ECS application secrets:
Step 1: Store Your Secrets
You can create parameters in AWS Parameter Store using the AWS Management Console, AWS Command Line Interface (CLI), or SDK.
Here’s a CLI example:
aws ssm put-parameter --name /HelloWorld/Port --value 3000 --type SecureString
Step 2: Grant IAM Permissions
Your ECS task execution role needs access to AWS Parameter Store. To enable this, update your existing role or create a new one. Then, attach an inline policy to grant ECS the necessary permissions. Here’s an example policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "ssm:GetParameters",
"Resource": "PARAMETER_STORE_VARIABLE_ARN"
}
]
}Step 3: Update Your Task definition
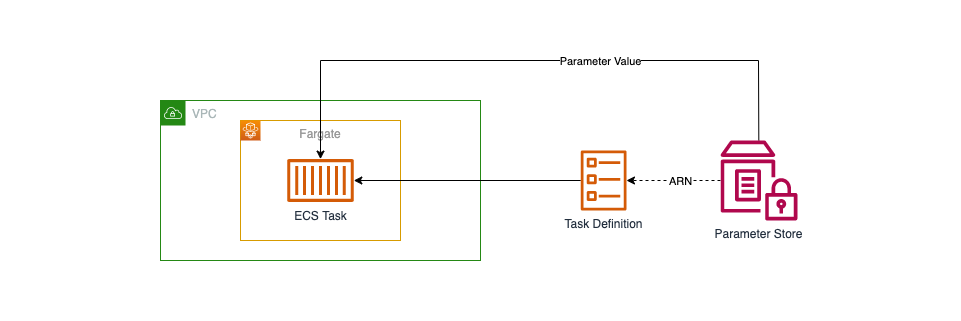
Within your task definition, use the updated task execution role and specify the ARN of your parameter. This step ensures that your service can access the secrets securely.
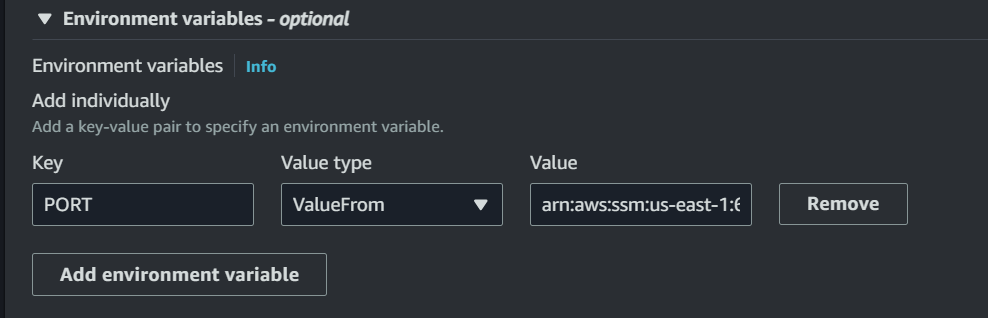
Now, you’re ready to create a service for your task. It will fetch secrets from Parameter Store, and even those who have access to your task definition won’t be able to view your application secrets.
Step 4: Update Secrets Easily
When you need to change a secret, simply make the update in Parameter Store. Your ECS tasks or services will automatically fetch the latest version, minimizing the need for manual updates.
Conclusion
Protecting your ECS application secrets is vital for maintaining the integrity of your cloud-based applications. AWS Parameter Store offers a user-friendly and secure solution, enabling you to focus on building and scaling your applications without compromising security.
